The DPIL Miner
As well as manually creating a DPIL model using the DPIL modeler, users can also discover models from event logs using the DPIL Miner. Here, the analyst selects the DPIL macros that should be discovered w.r.t. the provided event log. Both the execution engine and the mining module are based on the JBoss Drools platform that provides a current implementation of the rete rules solver. Therefore, in both components DPIL rules are transformed to the Drools Rule Language (DRL).
DPIL Miner Functionality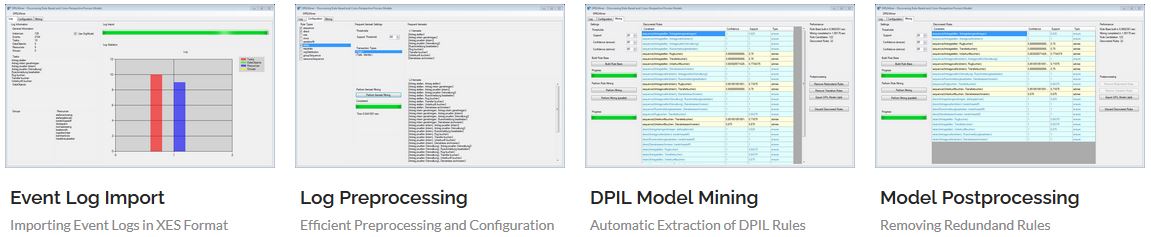
Background
For purposes of compliance and process improvement, organisations are interested in the way their processes are actually executed. Process mining aims at discovering processes by extracting knowledge from event logs, e.g., by generating a process model reflecting the behaviour recorded in the logs. Declarative languages like Declare or DPIL can be used to represent these models, and tools like DeclareMiner or MINERful to generate them, often with a focus on control flow and data. Agile processes, however, need to explicitly integrate the organisational perspective due to the importance of human decision-making and expert knowledge. Recent research has identified the potential of role mining and process mining of the organisational perspective. However, these results have not yet been integrated with declarative process models.
Solution
The DPIL Miner fills this research gap by proposing a process mining approach to discover resource-aware, declarative process models. In particular, we are able to extract complex allocation rules, such as binding of duties between activities, as well as cross-perspective rules involving the control-flow and the organisational perspectives together. The latter consider the influence of resource allocation on the control flow of the process, e.g., an activity can only be executed by a specific role if a specific activity was performed previously. The expressiveness of the extracted rules has been evaluated using the Workflow Resource Patterns. The applicability of the approach has been validated with a real-world event log from the university domain.
